TGCTF 2025 RE部分WP
re部分除了最后一道index都做了,index附件本身都跑不起来,而且wasm不好玩,不补了
水果忍者
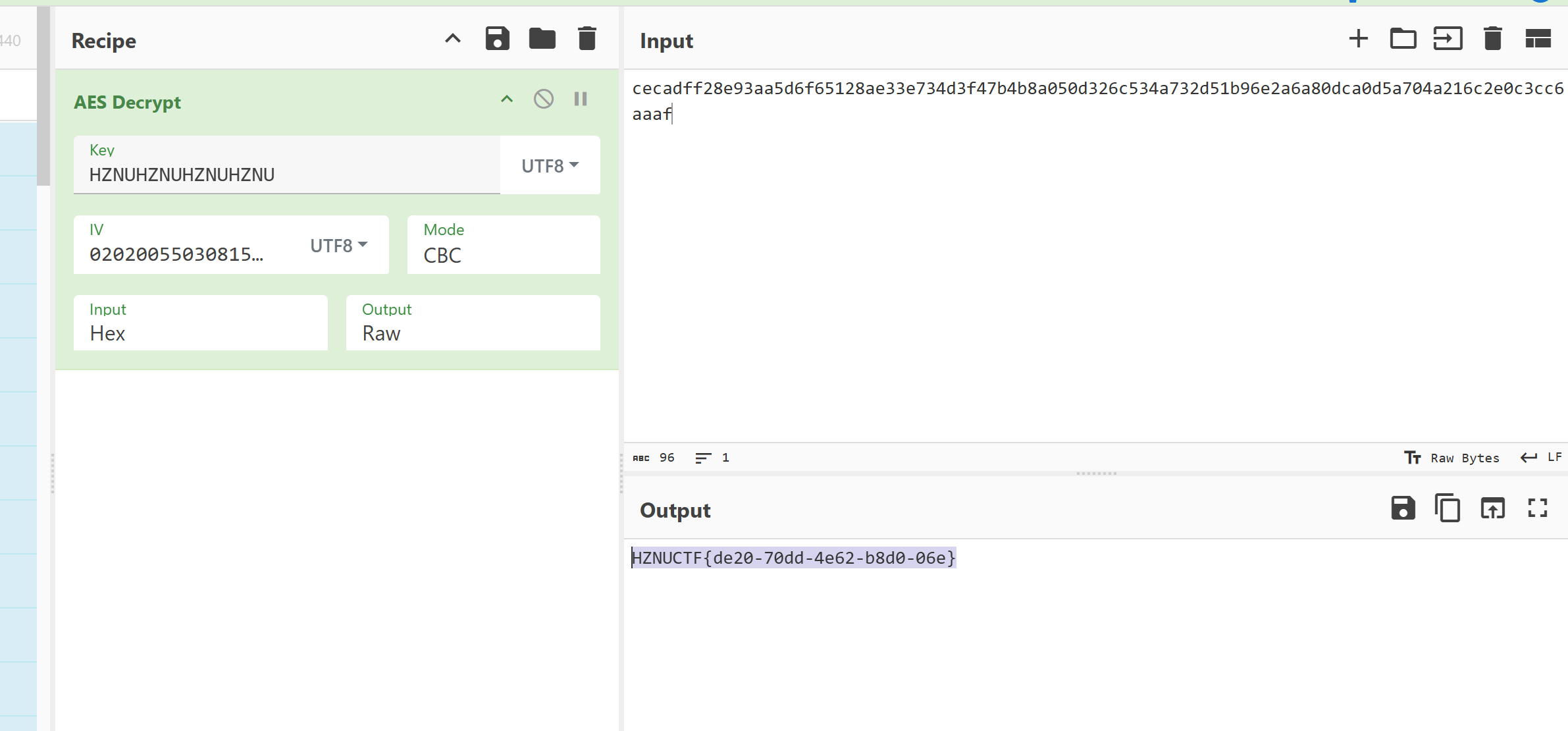
点进去直接就写明白了,iv,key和密文直接就有,cyberchef直接解
HZNUCTF{de20-70dd-4e62-b8d0-06e}
蛇年的本命语言1
先拿把exe解压一下拿到pyc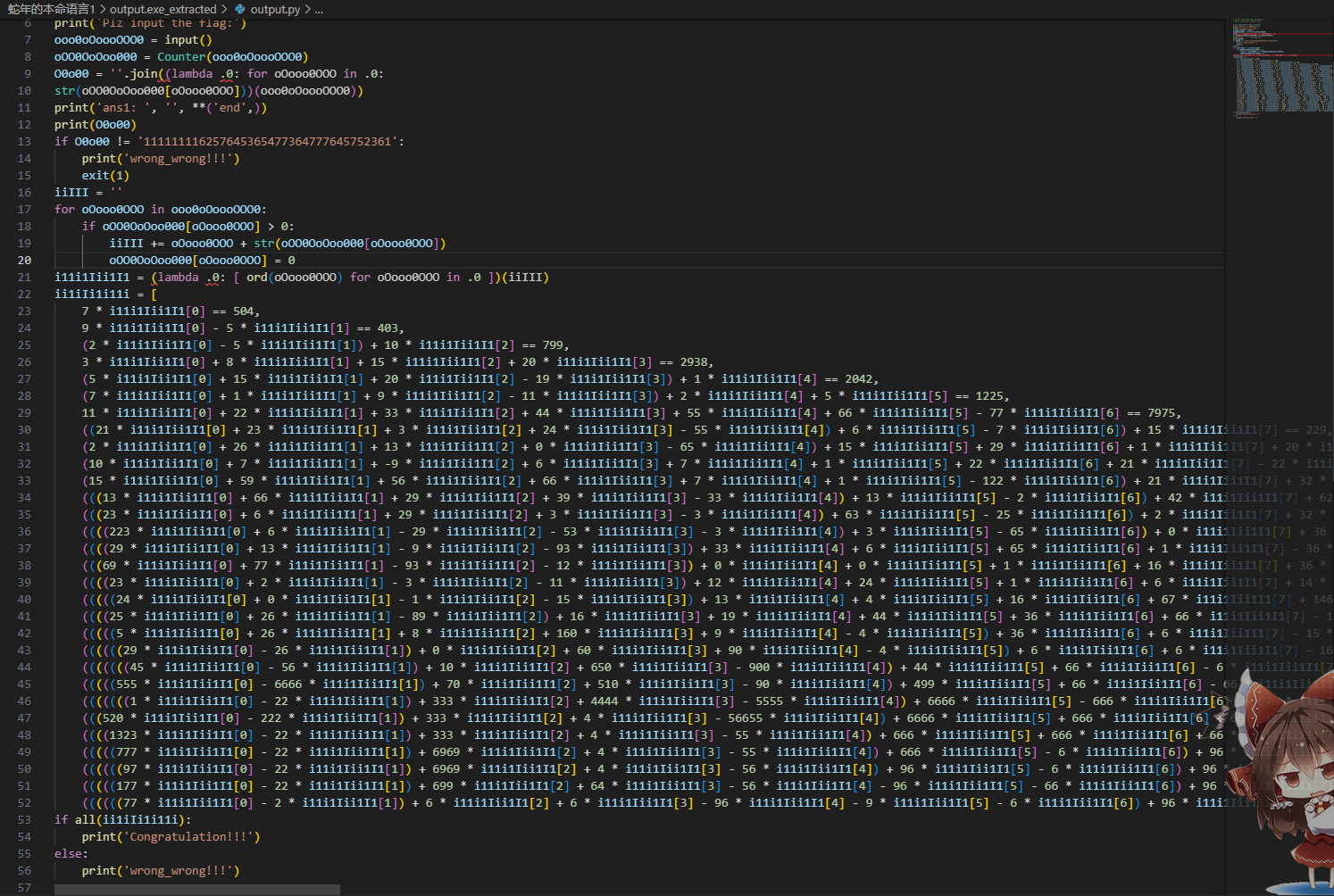
变量名混淆过,先整理一下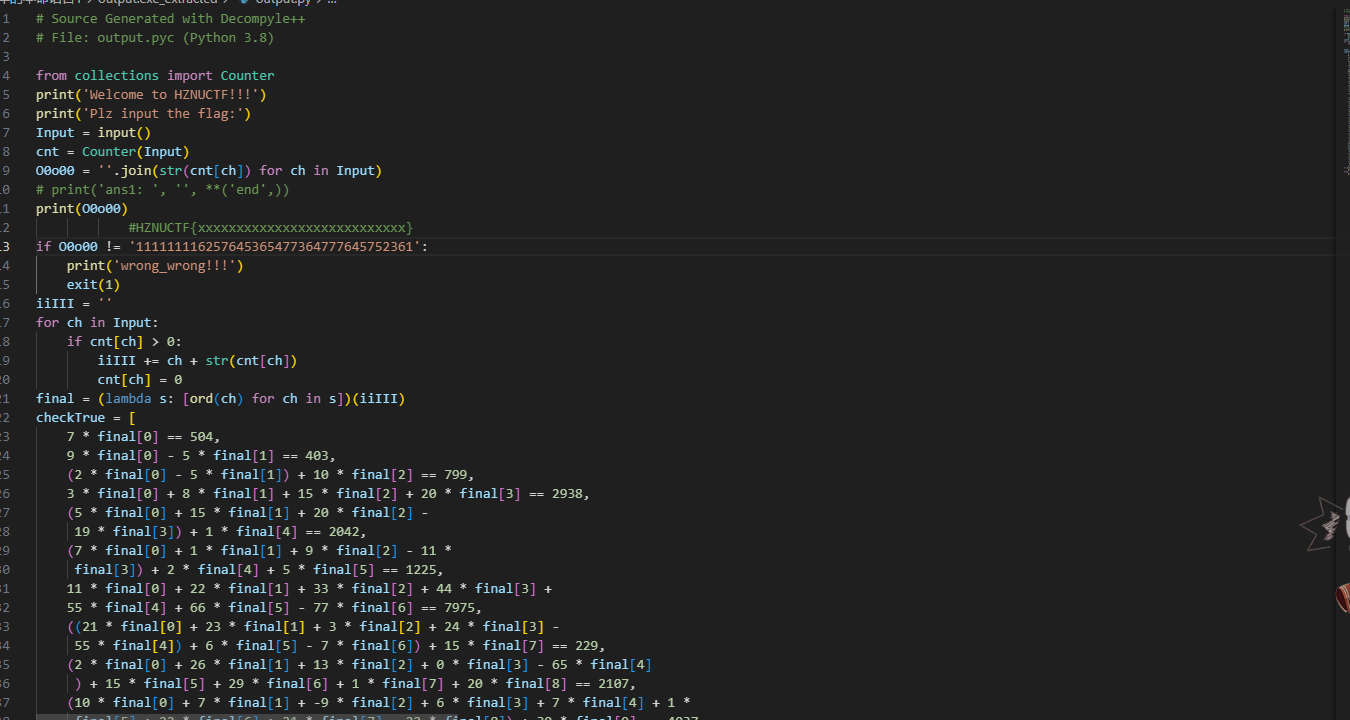
明显的z3,上面那个仔细观察后发现每个数字都对应一种字符的出现次数,结合z3求解
1 | from z3 import * |
解完后发现出现4次的字符对应的是不可见字符,可能是z3有多解,尝试爆破,试出来那个位置还有一种解是-
HZNUCTF{ad7fa-76a7-ff6a-fffa-7f7d6a}
randomsystem
点开有花,拿脚本去一去
1 | from binaryninja import * |
点开里面一大坨,但发现前面乱七八杂糟的都在初始化dest这个量,而这个量的预期值直接明文给出了,直接动调patch进入下面的逻辑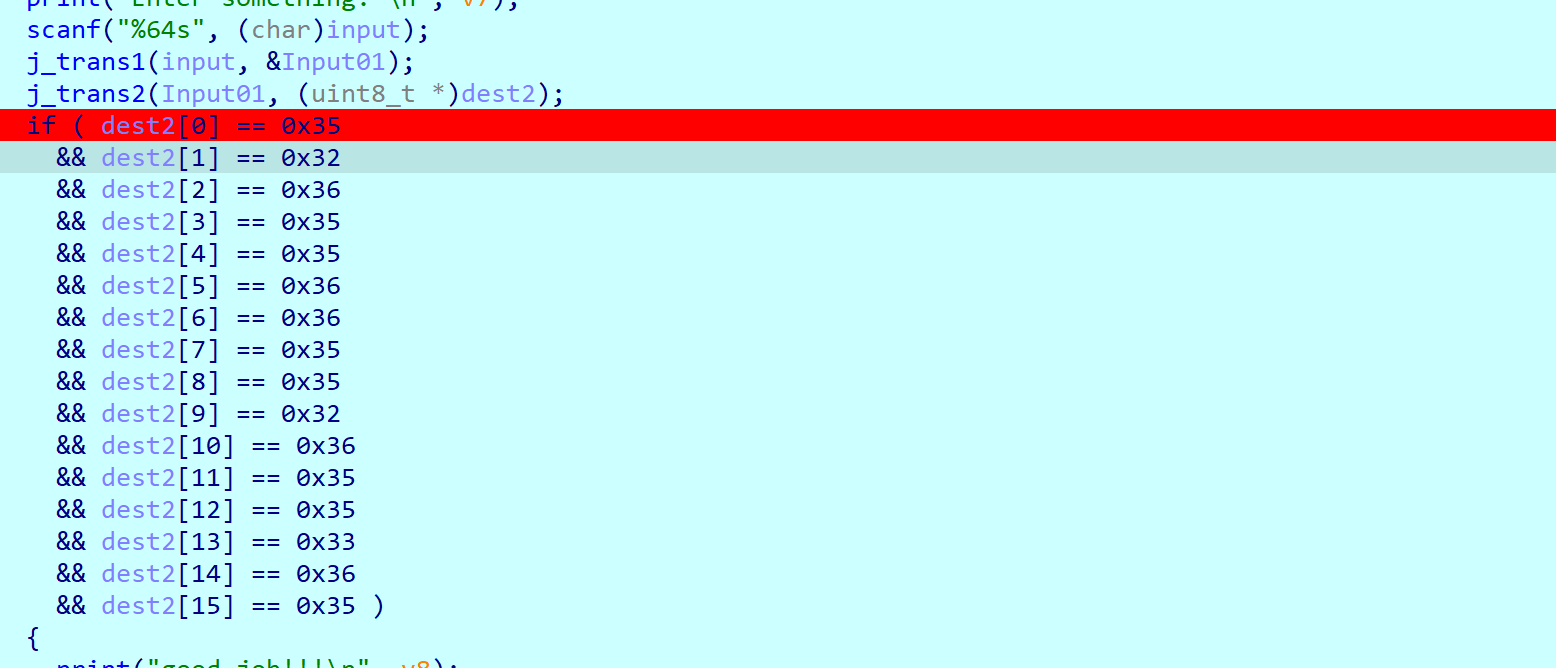
下面那个rand也不看,反正都是初始化,动调抓
最后是一个异或,key直接动调拿到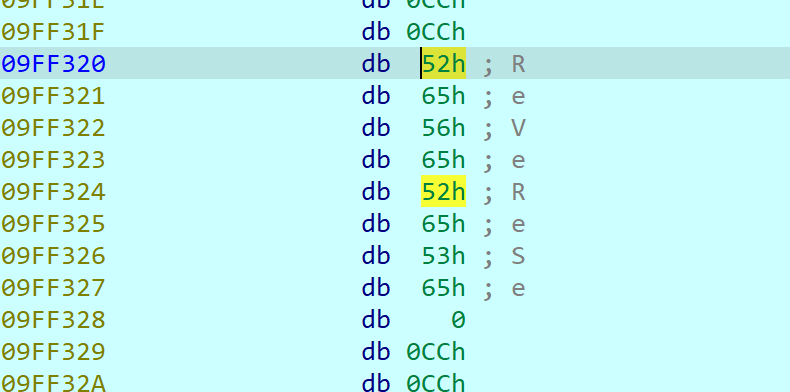
倒数第二个是一个矩阵乘,用z3反解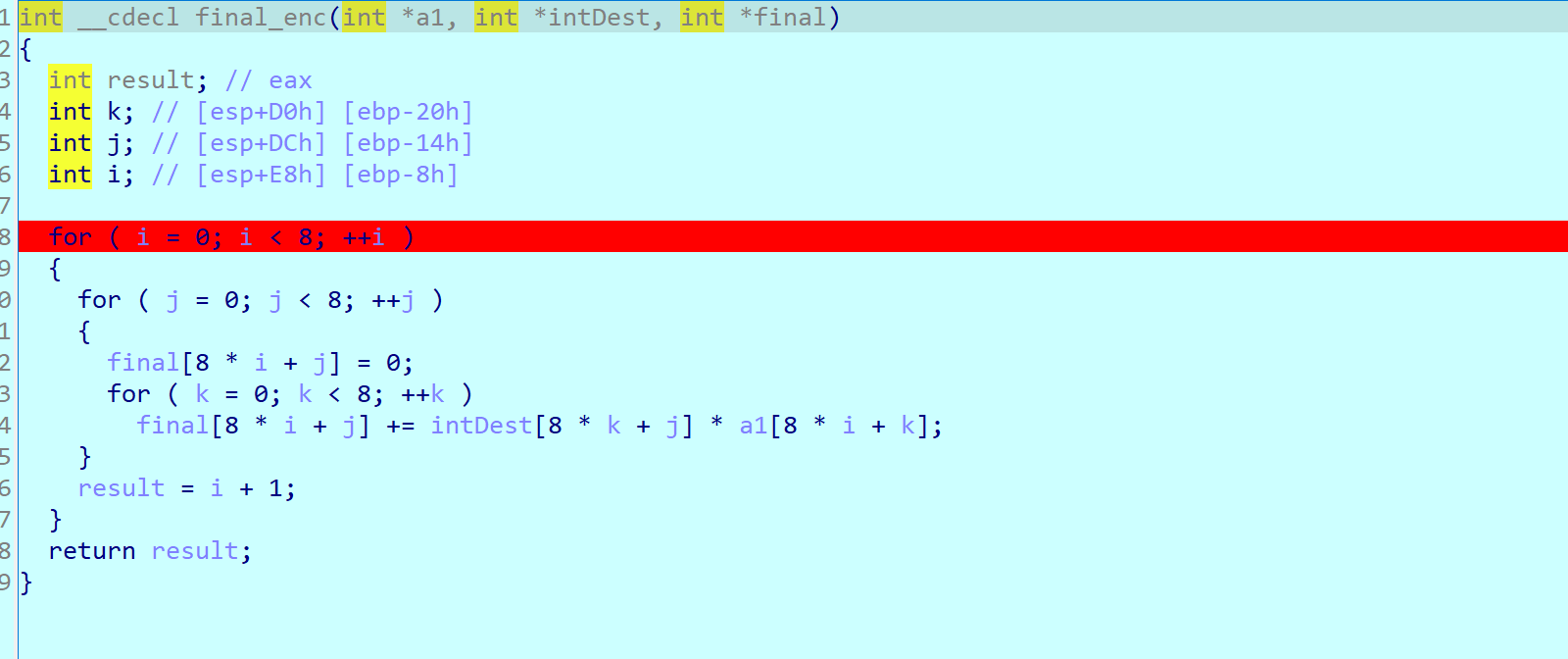
1 | from z3 import * |
解出fd11v56d454r6f4acb-1ea8d-6fy80795af83zfrb8-cd6cdc24tca7559fa099-
再往前就是交换混淆,这个直接往里面输入1,2,3,4,5…爆破交换映射
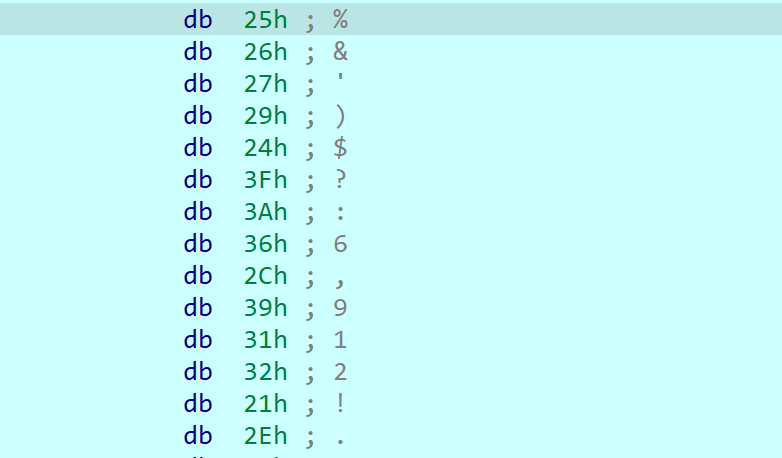
然后重新映射回去即可解出flag
1 |
|
HZNUCTF{3zfb899ac5c256d-7a8r59f0tccd-4fa6b8vfd111-a44ffy4r0-6dce5679da58}
exchange
打开有一个很奇怪的算法,对比下输入输出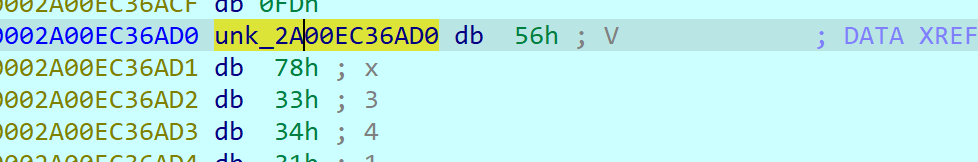
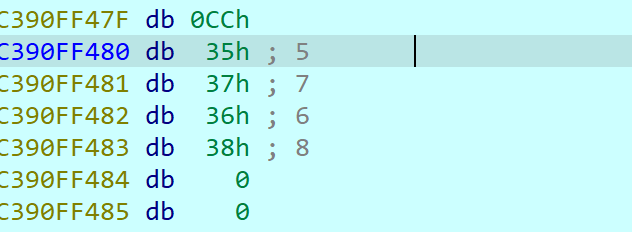
可以看到是把输入以4个16进制位为一组,交换中间的两位并转字符串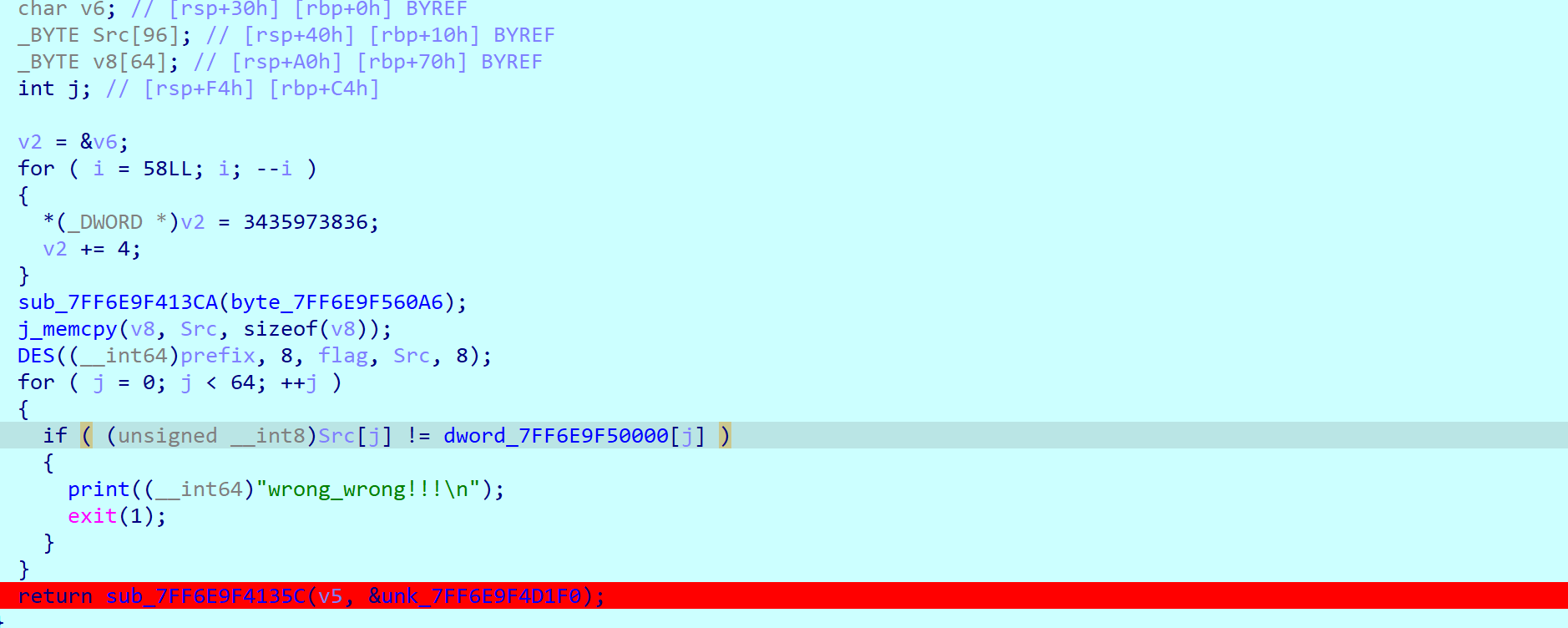
里面就是很明显的一个des,findCrypto可以找到盒
然后这个des是魔改过的,工具没法解,众所周知Fesitel网络密码只要把轮函数反过来跑就能解密,des就是把key倒过来用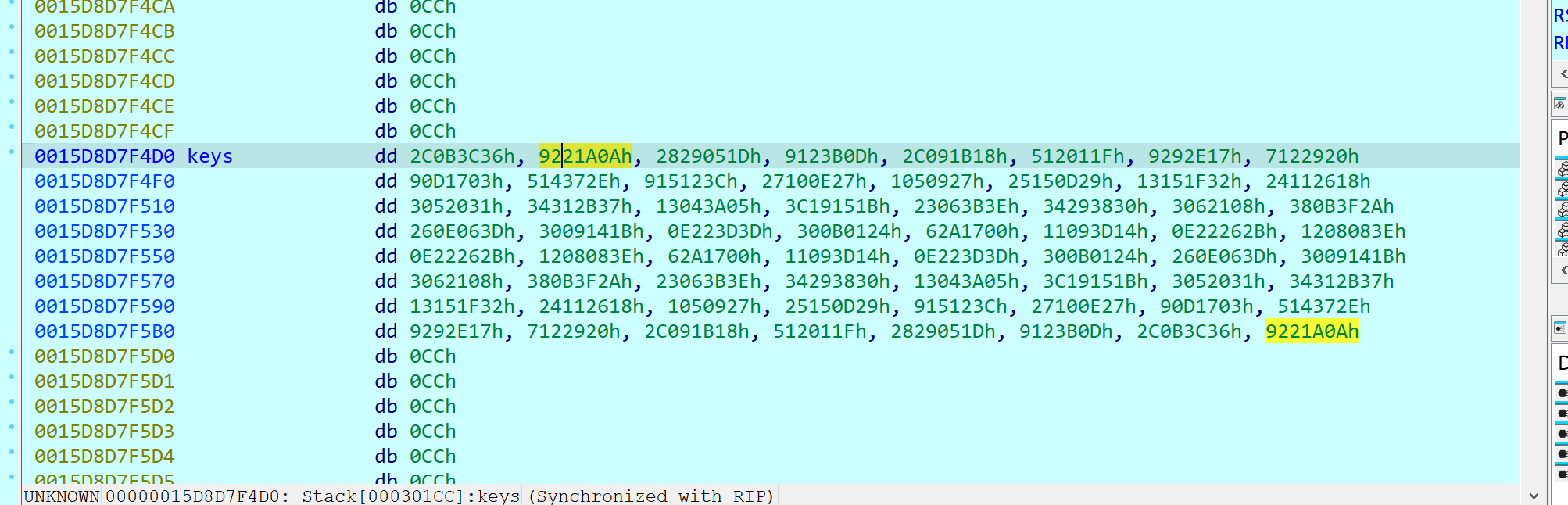
动调抓一下key,发现这个key似乎是对称的,而且组数也太多了点,合理怀疑这是一个加解密一体的算法,后半部分就是解密用的反key
直接把key的指针+32 (看一下当前传参时key的地址通过哪个寄存器转递,直接改寄存器值)
然后把密文patch进输入里跑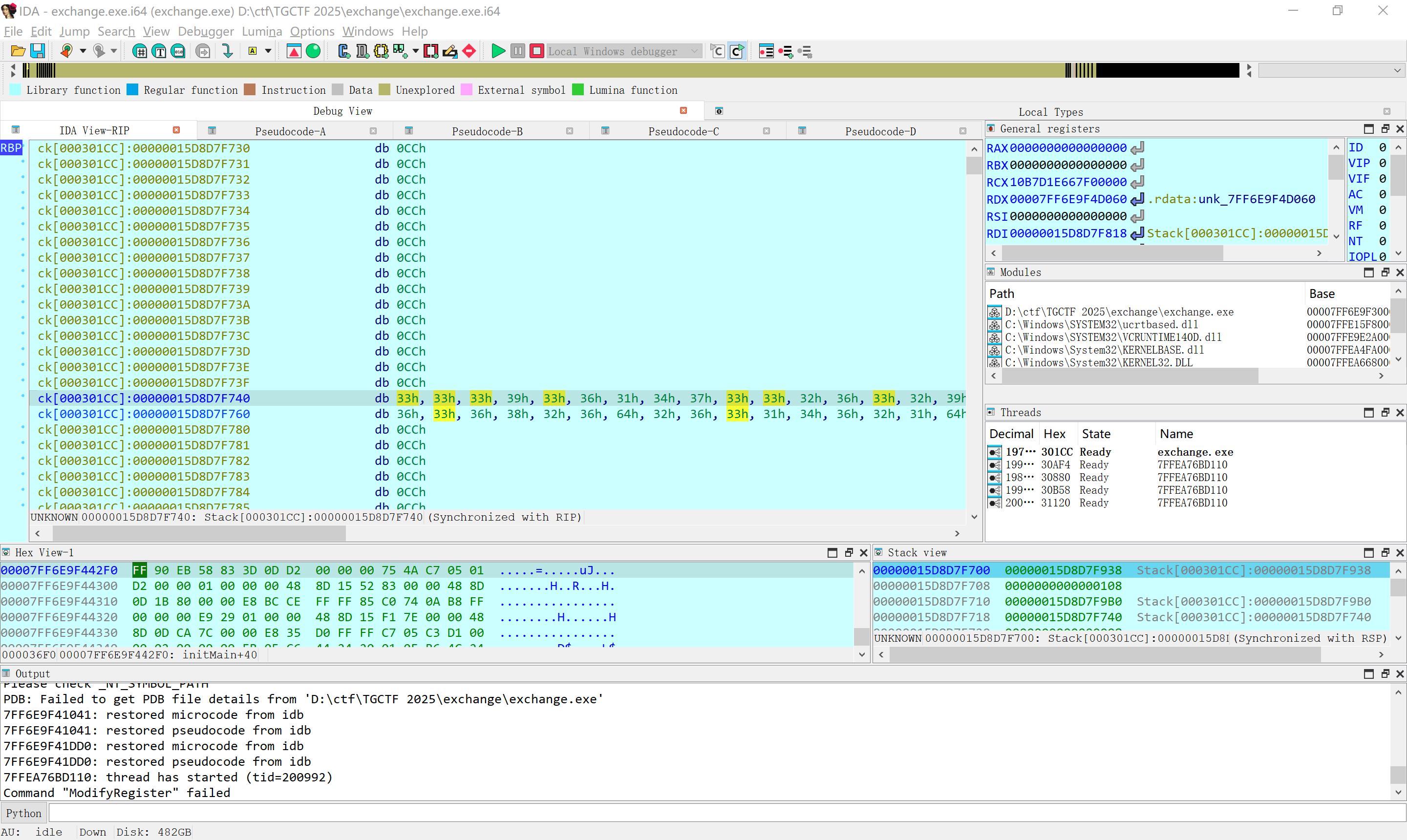
可以看到跑出来的结果十分好看
然后写脚本把换位改回去转成hex
1 | char mes[] = "333936147332632923d96353321d3345636826d26314621d3349330463126348"; |
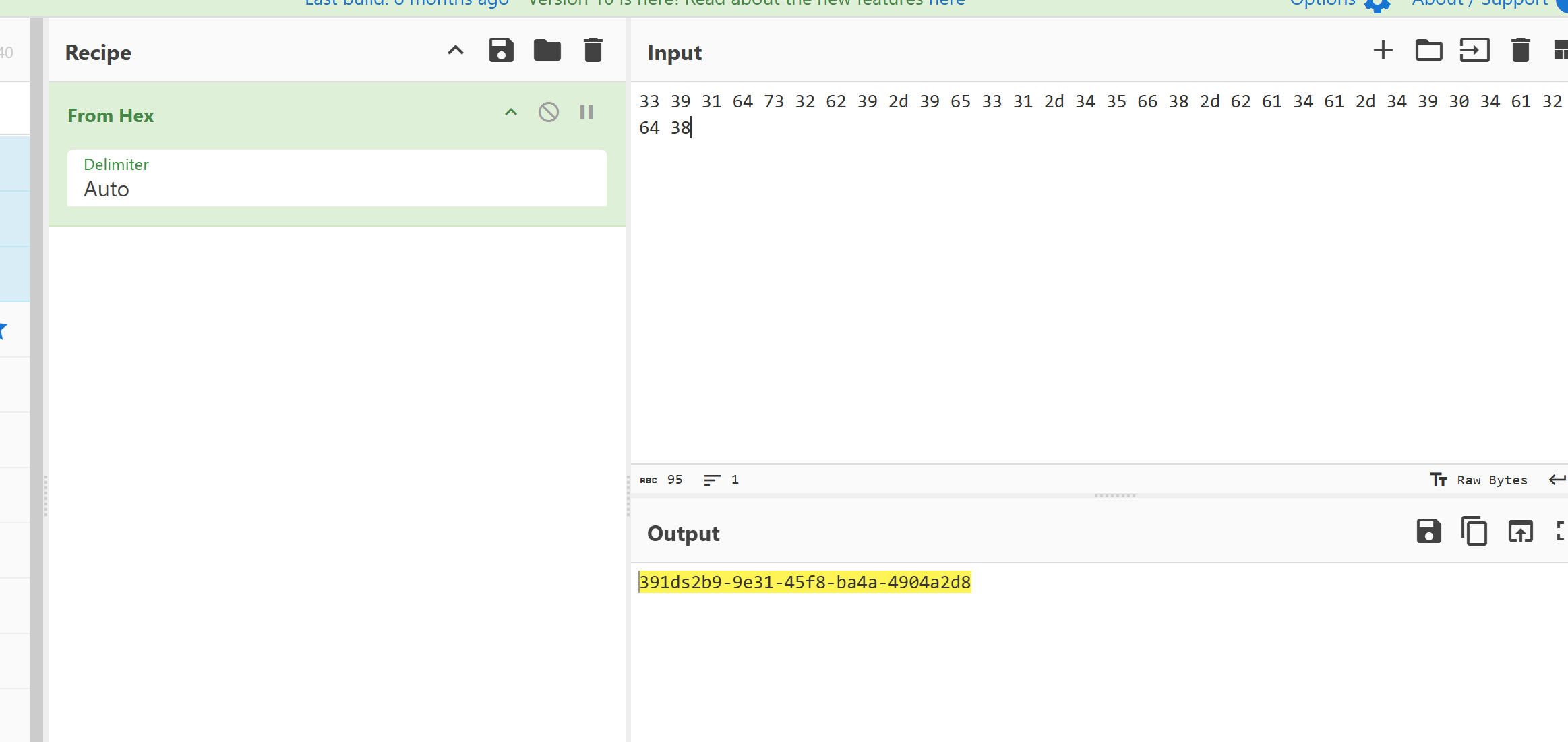
直接解出
xtea
cbc模式的xtea,直接进去抄源码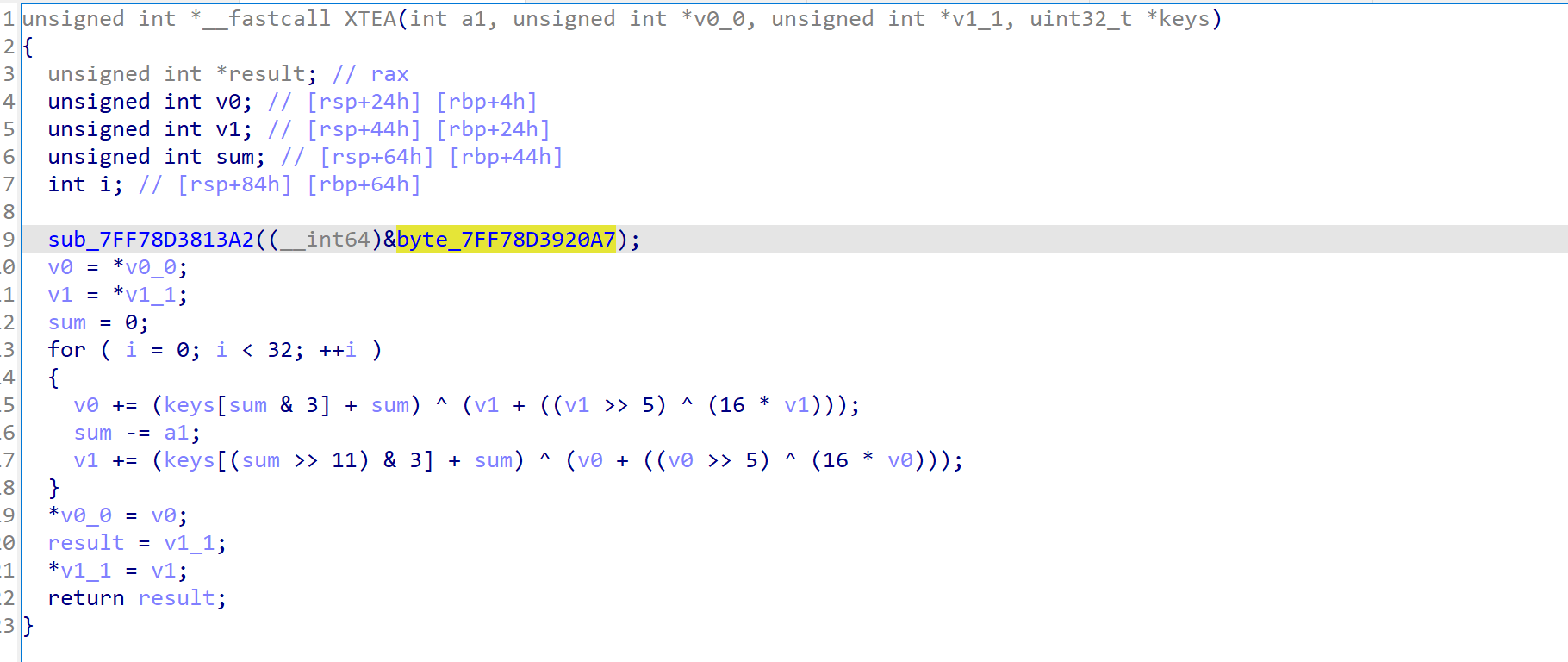
注意到这里有一个反调试,如果直接动调拿key的话种子不对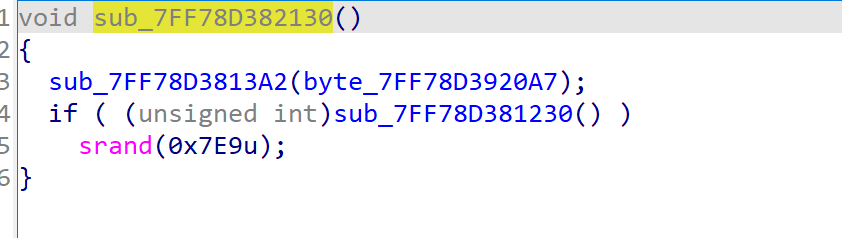
写脚本
1 |
|
HZNUCTF{ae6-9f57-4b74-b423-98eb}
conforand
die检测有ollvm,先尝试用d810解一下
解完还是很丑,每个函数都有几百行,但是出题人没删符号表,定位几个关键点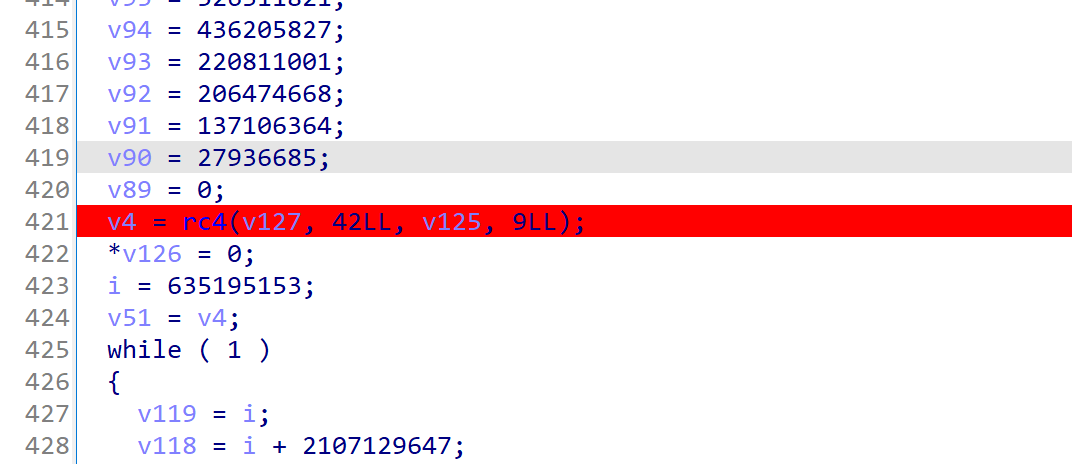
众所周知rc4跑两次等于没跑,所以我们尝试用frida去手动调用rc4
检查initbox的部分,发现引入了随机数种子,且种子未给出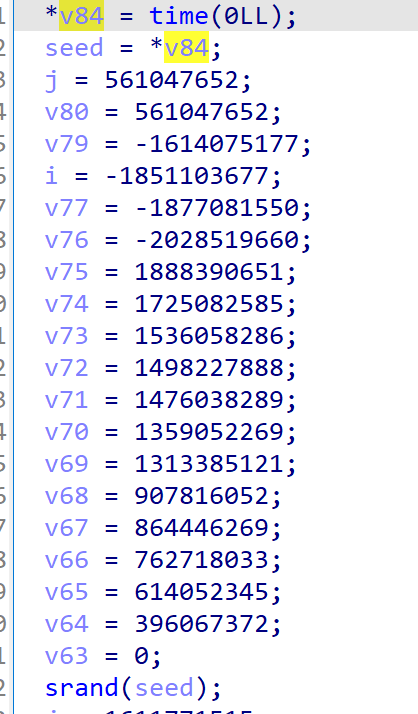
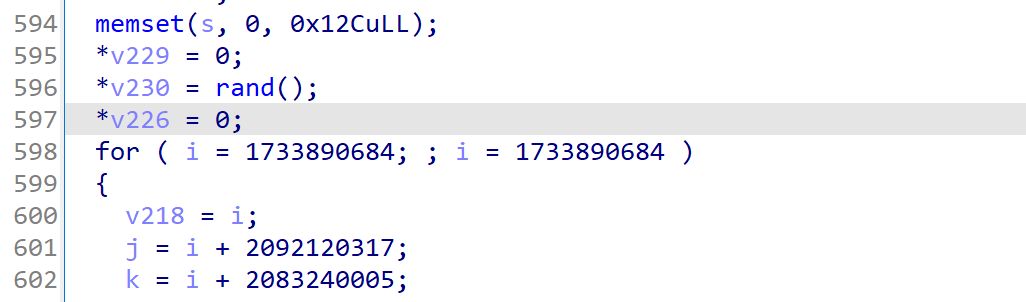
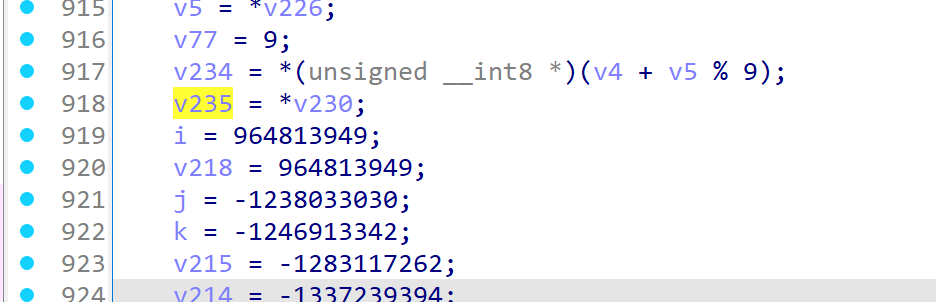
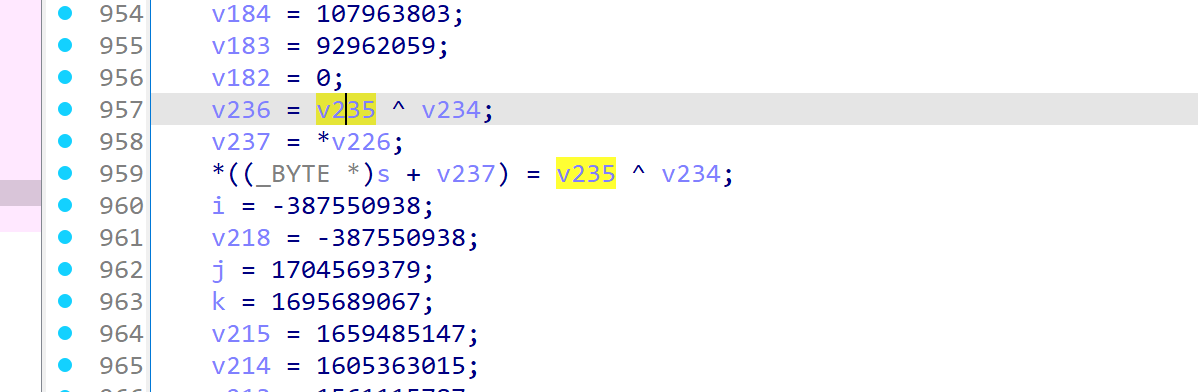
但注意到这个随机数的范围被限定在了0~255(S盒里的元素是uint8),且rand只调用了这一次
所以我们可以hook rand的返回值,爆破所有情况
写frida脚本
1 | var lib = Process.findModuleByName("conforand"); |
1 | import frida |
解出HZNUCTF{489b88-1305-411e-b1f4-88a3070a73}
TGCTF 2025 RE部分WP